
In the vast tapestry of history, threads of secrecy have woven their way through the annals of communication. As civilizations emerged and empires flourished, the need to safeguard sensitive information became paramount. In the realm of clandestine communication, one name stands out — Julius Caesar. Enter the world of “Caesar Cipher and Early Encryption Techniques,” a fascinating journey into the ancient art of securing messages.
This article embarks on a riveting exploration of the Caesar cipher, an ingenious encryption method devised by the legendary Roman general himself. But it doesn’t stop there; we delve into the broader landscape of early encryption techniques, unraveling the cryptographic mysteries that civilizations employed to protect their most guarded communications. From ancient scrolls to secret societies, this article is a key to unlocking the secrets of the past.
What to Expect:
- Caesar Cipher Unveiled: Discover the inner workings of the Caesar cipher, a cryptographic technique so simple yet powerful that it served as the cornerstone of clandestine communication during Julius Caesar’s era. We’ll walk you through the encryption and decryption processes, revealing the elegance in its simplicity.
- Mathematics of Secrecy: Delve into the mathematical underpinnings of the Caesar cipher. Unravel the modular arithmetic that transforms plaintext into ciphertext, and vice versa. See how a basic shift in the alphabet can create an impenetrable veil of secrecy.
- Advantages and Vulnerabilities: Explore the strengths and weaknesses of the Caesar cipher. Understand why it became a go-to for ancient civilizations and why, despite its simplicity, it fell prey to the evolving landscape of decryption techniques.
- Beyond Caesar: Early Encryption Techniques: The Caesar cipher may have been a gem in its time, but what about other methods employed by ancient cryptographers? From the transposition ciphers of the Spartans to the substitution ciphers of the Arabs, this article unveils the diversity of encryption methods that history has to offer.
- Relevance in the Modern World: While the Caesar cipher might seem like an ancient relic, its principles echo through time. Explore how the foundations laid by Caesar and his contemporaries still influence modern encryption protocols and the world of cybersecurity.
Embark on this historical voyage with us, where every encrypted message holds the whispers of a bygone era. From the battlefields of Rome to the corridors of power in ancient civilizations, “Caesar Cipher and Early Encryption Techniques” is your key to unlocking the secrets of the past and understanding the evolution of the clandestine dance between encryption and decryption. Get ready to uncover the veiled history of cryptographic artistry!
Table of Contents
Importance of Caesar Cipher
The exploration of the Caesar Cipher and early encryption techniques holds profound significance across various domains, making it an engaging area of study for several compelling reasons:
- Historical Significance: Unveiling the intricacies of ancient encryption methods provides a captivating journey into the history of human communication. The utilization of ciphers, exemplified by the Caesar Cipher, unveils insights into the challenges faced and strategies employed by civilizations in safeguarding sensitive information.
- Evolution of Cryptography: The Caesar Cipher stands as a pivotal milestone in the evolutionary path of cryptography. Serving as a foundational element, it lays the groundwork for the development of more intricate encryption techniques spanning centuries. Scrutinizing its principles allows us to trace the roots of contemporary cryptographic systems.
- Educational Value: Delving into early encryption techniques offers an exceptional educational opportunity. Whether for students or enthusiasts, this exploration introduces individuals to fundamental cryptographic concepts like substitution ciphers and modular arithmetic. Such knowledge forms a solid foundation for understanding advanced encryption protocols.
- Cybersecurity Insights: Understanding the vulnerabilities inherent in the Caesar Cipher and analogous techniques sheds light on the challenges faced by historical cryptographers. This comprehension significantly contributes to contemporary discussions on cybersecurity, guiding the development of robust encryption systems in the digital age.
- Cultural and Linguistic Context: Encryption methods often mirror the cultural and linguistic contexts of the societies that created them. Investigating these techniques opens a unique window into the linguistic structures and mathematical understanding of ancient civilizations, thereby enriching our appreciation of their intellectual achievements.
- Foundations of Cryptographic Principles: The Caesar Cipher introduces fundamental cryptographic principles such as key-based substitution and symmetric encryption, which remain integral to many cryptographic systems today. A grasp of these basics enhances comprehension of the broader field of cryptography.
- Practical Applications: Despite its apparent simplicity, the Caesar Cipher finds practical applications. It is still employed in educational settings to teach encryption concepts and in puzzle challenges that necessitate participants to decipher encoded messages. Recognizing the practical applications of early encryption techniques contributes to a well-rounded understanding of cryptography.
- Cultural Heritage Preservation: Encryption techniques represent a crucial part of our cultural heritage. Preserving and studying these methods is akin to safeguarding a piece of history. It allows us to appreciate the intellectual achievements of past civilizations and ensures that their contributions to the field of cryptography are not consigned to oblivion.
In summary, the importance of studying the Caesar Cipher and early encryption techniques extends beyond historical curiosity. It encompasses their historical, educational, and practical significance, emphasizing that these cryptographic methods are not mere relics of the past but the foundational elements upon which the complex structure of modern cryptography is built. This influence resonates in our understanding of security and communication in the digital age.
Caesar Cipher Unveiled: Exploring the Elegance in Simplicity
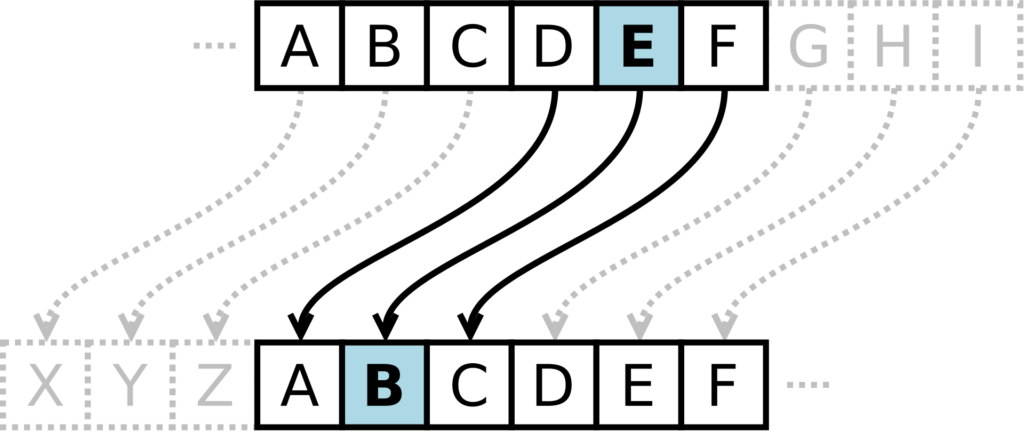
Within the enigmatic realm of ancient cryptography, the Caesar Cipher stands as an enduring testament to the artistry of secret communication. Delving into its intricacies not only reveals the ingenious simplicity woven into its design but also illuminates the historical significance embedded in the early tapestry of encryption techniques.
Deciphering the Core:
The Caesar Cipher, credited to the legendary Roman general Julius Caesar, operates on a fundamental principle—shifting letters along the alphabet. This ‘shift’ or ‘key’ dictates the displacement of each letter in the plaintext, creating a seemingly unreadable message. Envision a covert code exchanged among allies in an era when the destiny of nations teetered on the brink.
Encryption Ballet:
The encryption process, reminiscent of a meticulously choreographed dance, metamorphoses plain text into a covert arrangement. Picture this: ‘A’ transforms into ‘D’ with a shift of 3, ‘B’ morphs into ‘E,’ and so forth. Mathematically expressed as Eₙ(x) = (x + n) mod 26, where ‘x’ signifies the position in the alphabet, this process intricately weaves a coded tapestry.
Consider the simplicity of encrypting “HELLO” with a shift of 3. H becomes K, E turns into H, L shifts to O, and O transforms into R. Behold, the encrypted incantation reads “KHOOR.” The elegance lies in its simplicity — a ballet of letters gracefully pirouetting across the alphabet.
Decryption Symphony:
The decryption process gracefully reverses the encryption dance. Each letter twirls back to its original position with mathematical precision. Mirroring the encryption equation, Dₙ(x) = (x – n) mod 26, the Caesar Cipher elegantly unveils the concealed message. The encrypted “KHOOR” pirouettes back to its origin, revealing the hidden “HELLO.”
Elegance in Simplicity:
The beauty of the Caesar Cipher lies in its simplicity. At its core, it is a substitution cipher, replacing each letter with another predetermined letter. This simplicity, however, does not diminish its historical importance or educational value. Instead, it forms the cornerstone upon which complex cryptographic structures stand.
Beyond the Cipher:
As we unravel the mysteries of the Caesar Cipher, we embark on a journey beyond the mere mechanics of encryption. This ancient technique, with its limited key space and vulnerability, serves as a foundational stone for modern cryptographic principles. Its decryption holds the key to understanding the roots of cybersecurity and the evolution of the cryptographer’s art.
In the dance between encryption and decryption, the Caesar Cipher emerges as a timeless performer. Its elegance lies not only in its mathematical precision but also in its historical echoes. To explore the inner workings of the Caesar Cipher is to decipher a symphony of secrecy, where each shift and substitution resonates through the annals of cryptography, revealing the enduring allure of ancient encryption techniques.
Mathematics of Secrecy: Unraveling the Caesar Cipher
The Caesar Cipher, a cryptographic marvel employed by Julius Caesar himself, is not merely a historical curiosity but a mathematical enigma that opens a door to the fundamental principles of encryption. At its core lies the intricate dance of numbers and the artistry of modular arithmetic, transforming plaintext into ciphertext and vice versa. In this exploration, we delve into the mathematics of secrecy embedded in the Caesar Cipher, revealing how a basic shift in the alphabet can create an impenetrable veil of confidentiality.
Mathematics of Secrecy: Unraveling the Caesar Cipher
The Caesar Cipher, a cryptographic marvel employed by Julius Caesar himself, is not merely a historical curiosity but a mathematical enigma that opens a door to the fundamental principles of encryption. At its core lies the intricate dance of numbers and the artistry of modular arithmetic, transforming plaintext into ciphertext and vice versa. In this exploration, we delve into the mathematics of secrecy embedded in the Caesar Cipher, revealing how a basic shift in the alphabet can create an impenetrable veil of confidentiality.
Understanding Modular Arithmetic: The Cipher’s Mathematical Foundation
The backbone of the Caesar Cipher’s mathematical prowess is modular arithmetic. This concept, a branch of number theory, deals with the remainder when one integer is divided by another. In the context of the cipher, the alphabet becomes a cyclic set of integers, creating a loop where Z wraps around to A. This cyclic nature is the essence of modular arithmetic.
The encryption process can be expressed mathematically as En(x)=(x+n) mod 26, where x is the numerical representation of a letter, and n is the shift value. This formula encapsulates the essence of the Caesar Cipher, showcasing how each letter is shifted within the modular space of the 26-letter alphabet.
Deciphering the Shift: Decrypting with Modular Arithmetic
To decrypt the message, we employ the same principles of modular arithmetic. The decryption function
Dn (x)=(x−n) mod26 reverses the process, bringing the ciphertext back to its original form. An intriguing observation emerges: Dn(x)=E26−n(x). This symmetry highlights the cyclic nature of the cipher, offering a shortcut to decryption by merely adjusting the shift.
The Alphabetic Alchemy: Transforming Letters into Numbers
Before the magic of modular arithmetic unfolds, the letters of the alphabet must be transformed into numerical values. A simple scheme is employed: A is 0, B is 1, and so on, up to Z being 25. This conversion allows for seamless mathematical operations, converting the act of encryption into a series of elegant equations.
Creating the Veil of Secrecy: Encryption in Action
Armed with these mathematical tools, the Caesar Cipher performs its cryptographic dance. Taking a plaintext letter, converting it to a numerical equivalent, applying the modular arithmetic shift, and finally, transforming it back into a letter creates a process seemingly simple yet profoundly effective in concealing messages from unintended eyes.
Beyond Caesar: Exploring Variants and Enhancements
The mathematical elegance of the Caesar Cipher extends beyond its historical roots. The cipher serves as a canvas upon which modern encryption techniques are painted. Variants, such as multiple shift values or keywords, showcase the adaptability of the mathematical principles at play. This adaptability is crucial in the development of more secure cryptographic methods.
In conclusion, the Caesar Cipher’s mathematical underpinnings reveal a captivating world of modular arithmetic and alphabetic alchemy. What might seem like a basic shift in the alphabet unfolds into a symphony of mathematical operations, creating a timeless encryption technique. This exploration not only illuminates the secrecy of Caesar’s messages but also opens a gateway to the broader realm of cryptography, where mathematical principles continue to shape the way we secure information in our digital age.
Advantages and Vulnerabilities:
In this section, we will delve into the strengths and weaknesses of the Caesar Cipher, unraveling the reasons behind its historical prominence and eventual decline in the realm of encryption. Explore how its simplicity became an asset for ancient civilizations, yet ultimately rendered it susceptible to the relentless evolution of decryption techniques.
Advantages of the Caesar Cipher:
- Simplicity and Ease of Use:
- The Caesar Cipher’s primary strength lies in its simplicity. It is easy to understand and implement, making it accessible to individuals with limited cryptographic knowledge. This simplicity contributed to its widespread use in ancient civilizations.
- Physical Implementation:
- The Caesar Cipher could be physically implemented using various tools, such as rotating disks or sets of cards, known as a scytale. This feature made it practical for use in situations where sophisticated cryptographic instruments were not available.
- Limited Pre-shared Information:
- The cipher requires minimal pre-shared information – just the knowledge of the shift value. This characteristic made it suitable for scenarios where distributing complex keys was impractical. Ancient civilizations could easily communicate using a shared understanding of the shift value.
- Educational Tool:
- Due to its simplicity, the Caesar Cipher serves as an excellent educational tool for introducing individuals to the concept of encryption. It remains a popular choice for teaching cryptographic principles and basic encryption techniques.
- Modifiability for Enhanced Security:
- The Caesar Cipher can be easily modified to create more secure variants. Introducing multiple shift values or using keywords can enhance its resistance against basic decryption attempts. This adaptability allowed ancient civilizations to tweak the method for improved security.
Vulnerabilities and Why It Fell Out of Favor:
- Susceptibility to Brute Force Attacks: The Caesar Cipher has a very limited keyspace of only 26 possible keys, corresponding to the number of letters in the English alphabet. This makes it vulnerable to brute force attacks, where an attacker can systematically try all possible keys until the correct one is found.
- Known-Plaintext Attacks: The cipher is susceptible to known-plaintext attacks, wherein an adversary has access to both the encrypted and unencrypted versions of the same message. This vulnerability compromises the security of the system, especially when patterns in the plaintext can be exploited.
- Inadequate for Long Text Encryption: The Caesar Cipher is not suitable for encrypting long texts. Its limited keyspace and vulnerability to brute force attacks mean that, over time, decrypting longer messages becomes increasingly feasible for an attacker.
- Lack of Confident Security Features: The Caesar Cipher does not provide confidentiality, integrity, or authenticity in a message. In modern cryptographic terms, it lacks essential security features required for secure communication, making it unsuitable for protecting sensitive information.
- Evolution of Decryption Techniques: As cryptanalysis evolved, especially with the development of more advanced mathematical and computational methods, the vulnerabilities of the Caesar Cipher became more apparent. Techniques like frequency analysis, which analyzes the occurrence of letters, could easily break the cipher.
- Rise of More Secure Encryption Methods: With the need for stronger and more secure encryption in the face of advancing decryption techniques, ancient civilizations and later cryptographers turned to more sophisticated methods. The Caesar Cipher, while historically significant, became obsolete for securing sensitive information in modern contexts.
In essence, the Caesar Cipher’s advantages lay in its simplicity and ease of use, making it a practical choice for ancient civilizations. However, its vulnerabilities, particularly against brute force and known-plaintext attacks, led to its eventual decline as more secure encryption methods emerged to meet the demands of evolving cryptographic landscapes.
Beyond Caesar: Early Encryption Techniques:
Beyond the famed Caesar Cipher, ancient cryptographers employed a variety of ingenious techniques to secure their messages. Two notable methods from different civilizations are transposition ciphers, notably used by the Spartans, and substitution ciphers, favored by the Persians.
Substitution Ciphers of the Persians:

The Persians, known for their advanced civilization and contributions to various fields, favored substitution ciphers in their cryptographic practices. Substitution ciphers involve replacing each letter in the plaintext with another letter according to a predetermined key.
How Persians Used Substitution:
Persian cryptographers would have a specific key or rule for replacing each letter in the alphabet with another letter.
This key served as the secret code to encrypt and decrypt messages, known only to the intended recipients.
The Persian substitution ciphers were likely more complex than the Caesar Cipher, involving intricate patterns and rules for letter substitution.
Historical Significance:
The Persian use of substitution ciphers reflects the sophistication of ancient cryptographic techniques.
It highlights the role of cryptography not only in military communications but also in diplomatic and administrative exchanges within the Persian Empire.
Transposition Ciphers of the Spartans:
The Spartans, known for their military prowess and strategic thinking, employed transposition ciphers as part of their communication strategy. Transposition ciphers involve rearranging the order of letters in a message without altering the actual letters themselves. This method added an extra layer of complexity to the encryption process.
How Spartans Used Transposition:
The Spartan transposition cipher involved systematically rearranging the letters of a message according to a predetermined pattern or key.
This rearrangement made the original message unintelligible without the knowledge of the specific transposition pattern.
The complexity of deciphering increased as the patterns became more sophisticated, providing the Spartans with a tactical advantage in securing their military communications.
Historical Significance:
The use of transposition ciphers by the Spartans illustrates the importance of strategic communication in military operations.
It showcases the adaptability of ancient cryptographers, who explored various methods beyond simple substitution to protect sensitive information.
Legacy and Lessons:
Exploring these transposition and substitution ciphers from ancient civilizations provides valuable insights into the diversity of cryptographic methods employed in different cultural and historical contexts. The legacy of these early encryption techniques extends beyond their specific applications, influencing the development of more advanced cryptographic systems throughout history.
Understanding the strategies of ancient cryptographers allows us to appreciate the intellectual challenges they faced and the inventive solutions they devised to safeguard information. These techniques laid the groundwork for the rich tapestry of encryption methods that continue to evolve in the digital age.
Relevance in the Modern World: Unveiling the Timeless Influence of the Caesar Cipher

Embarking on a journey through the labyrinth of cybersecurity and encryption, we find ourselves tracing the echoes of antiquity in the timeless influence of the Caesar Cipher. In a world where the rapid evolution of technology shapes our digital landscape, the simplicity of this ancient cryptographic technique might seem out of place. However, beneath its seemingly archaic exterior lies a foundation that has left an indelible mark on the very fabric of contemporary cryptography. Join us as we unveil the relevance of the Caesar Cipher in the modern age and explore how its ancient lessons continue to shape the way we secure information today.
1. Symmetric Encryption Principles:
At the heart of the Caesar Cipher lies the fundamental concept of symmetric encryption, where a single key serves the dual purposes of encryption and decryption. Astonishingly, this age-old principle remains a cornerstone of modern cryptographic systems. The Advanced Encryption Standard (AES) and numerous other contemporary algorithms still adhere to the symmetric key model, underscoring the enduring significance of the Caesar Cipher’s influence.
2. Building Blocks of Substitution Ciphers:
Delving into the realm of substitution ciphers, to which the Caesar Cipher belongs, reveals their integral role in modern cryptography. Although today’s ciphers have evolved beyond simple letter substitutions, the essence of replacing elements within a message for confidentiality persists. Understanding the Caesar Cipher provides a historical perspective on the evolution of substitution techniques that underpin modern cryptographic strategies.
3. Educational Significance:
The Caesar Cipher stands as a stalwart pedagogical tool, serving as the gateway for individuals venturing into the intricate world of cryptography. Educational institutions and cybersecurity training programs leverage its simplicity to impart foundational knowledge. Aspiring cryptographers, by studying the Caesar Cipher, gain invaluable insights into encryption concepts that serve as the building blocks for more sophisticated algorithms.
4. Vulnerability Awareness:
The vulnerabilities embedded within the Caesar Cipher, notably its susceptibility to brute force attacks, offer a crucial lesson for modern cryptographers. Acknowledging these weaknesses becomes the catalyst for the development of encryption methods that proactively address historical shortcomings. The study of vulnerabilities emerges as a linchpin for enhancing the resilience of contemporary cryptographic systems.
5. Cultural and Linguistic Context:
Beyond its cryptographic function, the Caesar Cipher reflects the cultural and linguistic context of its time. It highlights the intricate interplay between encryption methods and human language, emphasizing the modern need for algorithms that are not only secure but also culturally sensitive. Understanding linguistic nuances proves vital in the development of encryption protocols that align with diverse global communication patterns.
6. Cryptographic Evolution:
The trajectory from the Caesar Cipher to contemporary encryption algorithms mirrors the broader evolution of cryptography. Drawing wisdom from the past facilitates the refinement of cryptographic techniques. The principles laid down by Caesar and his contemporaries serve as a historical roadmap guiding the development of encryption protocols that seamlessly meet the demands of the digital age.
7. Practical Applications in Challenges and Puzzles:
Transitioning from theory to practice, the Caesar Cipher finds application in educational challenges and puzzles. Its inherent simplicity makes it an ideal tool for engaging individuals in deciphering encoded messages, fostering a hands-on understanding of encryption principles. Beyond the theoretical realm, the Caesar Cipher proves its mettle in cultivating practical skills and problem-solving acumen.
In conclusion, the Caesar Cipher, though ancient in origin, stands as a resilient pillar in the edifice of contemporary cryptography. Its enduring principles not only influence educational curricula but also permeate the design of sophisticated encryption algorithms. Recognizing the timeless relevance of the Caesar Cipher provides a profound appreciation for the enduring impact of early encryption techniques on the intricate tapestry of cybersecurity in the modern world.

Conclusion
This article unveils the fascinating world of ancient cryptography, with a particular focus on the ingenious Caesar Cipher. The narrative takes readers on a historical journey, exploring the significance of secrecy in communication throughout civilizations. Beyond unveiling the mechanics of the Caesar Cipher, the article delves into broader early encryption techniques, such as substitution and transposition ciphers.
The article provides a detailed understanding of the strengths and weaknesses of the Caesar Cipher, emphasizing its historical prominence and subsequent decline. It sheds light on the cipher’s advantages, such as simplicity and ease of use, while also addressing vulnerabilities like susceptibility to brute force attacks and known-plaintext vulnerabilities.
Furthermore, the exploration extends beyond Caesar, delving into the Persian use of substitution ciphers and Spartan deployment of transposition ciphers. These examples illustrate the diverse strategies ancient cryptographers employed to secure messages, showcasing the rich tapestry of early encryption methods.
The relevance of these ancient techniques in the modern world is highlighted, emphasizing their impact on contemporary cryptographic principles. The article underscores the enduring influence of the Caesar Cipher, from its role in educational settings to its practical applications in challenges and puzzles. It also explores the broader implications for cybersecurity, demonstrating how lessons from early encryption techniques continue to shape modern encryption protocols.
In summary, the article offers a comprehensive and engaging exploration of the Caesar Cipher and early encryption techniques, emphasizing their historical, educational, and practical significance in the evolving landscape of cryptography.
